Making Sense of bCrypt

I hate to tell you, but hashing passwords is no longer enough. Hackers have discovered how to combat even the strongest of hashing algorithms. Hackers utilizing Rainbow Tables, large tables of pre-computed hash digests, can compare and crack passwords faster than ever. If password security wasn't hard enough, it just got worse.
All hope isn't lost. There is an answer to the disarray caused by rainbow tables. Not to be confused with table salt, rock salt, or sea salt, password salts are made to obfuscate hash digests. By generating values that are non-standard to an algorithm, rainbow tables quickly become obsolete. You may be asking yourself, "but I don't enter a salt when I enter my password to Facebook! How does this all work?"
Enters our unsung hero, bCrypt. bCrypt is a Blowfish-inspired password-hashing function containing several features to keep prying eyes away from our precious passwords. Following the previous discussion, bCrypt auto-magically creates a randomized salt for every use. Therefore, even when the same plaintext appears in the bCrypt algorithm- the hash digest is unique. Here's a small example of this utilizing the mkpasswd command and the plaintext "password123".
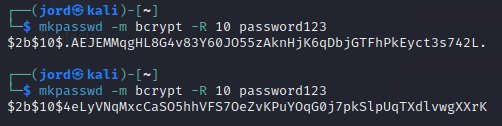
bCrypt can look confusing at first glance but stick with me. The bCrypt algorithm doesn't just plainly output a hash digest. Instead, it uses the dollar sign ("$") to denote different segments. The first segment, "$2b$", is used to identify the hashing algorithm- bCrypt. The second segment, "$10$," displays the "cost" of the algorithm. Our bCrypt digest tells us that this specific algorithm used 2^10 (1024) rounds of hashing. The rest of the digest is just a digest, or is it?
Let's take a second to think. By design, assuming the same input, hashing algorithms are designed to output the same value every time. So how can you verify a valid password for a web application using the bCrypt algorithm? Most of the confusion around bCrypt comes from these small details.
Not denoted by a dollar sign, there is a third and fourth segment to the output. The third segment is a twenty-two-character salt value that becomes concatenated with our original plaintext. It's evident now that "AEJEMMqgHL8G4v83Y60JO5" is the salt for the first hash digest in our previous example. Yes, the only way to figure that out is to count- unless you're a computer or good at guessing. The fourth segment is just the bCrypt digest of the original plaintext with the salt. Let's try to generate two identical hashes by using the same salt and the -S switch with mkpasswd.
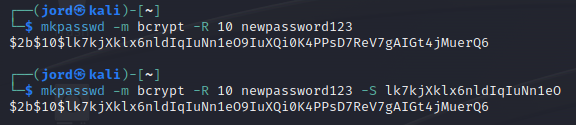
Okay, that wasn't too hard. To quickly recap, bCrypt denotes different segments using the dollar sign. The third segment is the salt value added to the original plaintext. The fourth segment is the actual hash digest output by bCrypt. What other security features does bCrypt implement to beef up our password security?
As stated previously, the Blowfish encryption algorithm inspired the creation of bCrypt. A critical piece of Blowfish is the expensive cryptographic key process. Knowing how the process works under the hood isn't necessarily important to understand. What should be understood is that a more expensive process makes potential brute-force attacks against Blowfish significantly slower. David Mazières and Niels Provos, the authors of bCrypt, understood the value of this process and implemented it within bCrypt. What does that mean for the average user? Despite rainbow tables, passwords have never been as secure as they are today- thanks to bCrypt!
Comments ()