
Hashes are, to put it bluntly, the backbone of modern day password security. Whether you’re signing into your local Windows machine, remotely SSH-ing into your Ubuntu VPS, or just logging into Facebook, hashes keep prying eyes away from your password. Without hashes you could say farewell to ever safely interacting with another login prompt again. With all this talk about safety and security, you may ask, why are we discussing cracking them?
Well, as is everything, hashes do have one major downfall. Hashes by design are only as strong as the plaintext you place into the mathematical magic that is the hashing algorithm. As much as the general user has been educated about password security and encouraged to follow it, we as hackers know this to be a pipe dream. Don’t believe me? I encourage you to go interrogate your family members for their Amazon account passwords. Bonus points if you discover a loved one still operating with a Yahoo email address!
Okay, now we know that a hash is equivalent in strength to the password that it represents. What exactly does that mean? This is where a lot of beginner cybersecurity enthusiasts mix-up the difference between hashing and encryption. Unlike encryption, hashes are designed to create the same output, assuming the same input, every single time. When we use an MD5 hashing algorithm, for example, and we hash a super secure password such as “password123” we’ll get “482c811da5d5b4bc6d497ffa98491e38” output every time. In layman’s terms, by generating a matching hash you have essentially found the original plaintext. Doing this manually would take well beyond a human’s lifespan, if only we had a means to generate hashes at inhuman speeds then check it against the targeted hash comparing until we received a match. I guess we’ll never crack my super secure password.
That’s what you would say, if you didn’t know how to use Hashcat. Hashcat is, by the authors words, “the world’s fastest and most advanced password recovery tool.” To make it even easier to use Hashcat, Hashcat comes pre-installed on every instance of Kali Linux. Just as a benchmark for those who have never used Hashcat, my non-optimized Gigabyte RTX 3070 graphics card scored around 41,000 MH/s against a standard MD5 hash. Taking after standard computing terminology, “MH” represents millions, therefore our final number of MD5 hashes cracked per second is give or take 41,000,000,000 (41,000 * 1,000,000). In non-nerd terms, your moms Pinterest password is quivering in fear of the harnessed modern day computing power made possible by Hashcat.
**
Tip: Want to benchmark your own system? Use Hashcat’s benchmark feature by utilizing the “-b” switch when initiating Hashcat. You can also find other users benchmarks online via the Hashcat wiki to compare your hardware with other Hashcat users!
**
For this example I’m going to be matching up my previously discussed, super secret, “password123” password against Kali Linux’s standard rockyou.txt wordlist. Upon firing up the Hashcat help menu, as you should with any tool you’re unfamiliar with, you’ll be greeted with pages of unique options. Basically, Hashcat needs a little bit of information from you, its trusted wielder, before it wages all-out war against an unsuspecting hash. To utilize a dictionary style attack, A.K.A taking input from a plaintext text file, we need to tell Hashcat three things, what kind of hash we’re going to be cracking, a file with the targeted hash written inside, and the wordlist we’re going to be using to make guesses at the targeted hash.
**
Tip: You can use Hashcat’s built-in example hashes to figure out which hash mode you need. Execute Hashcat with the “–example-hashes” switch to see all supported hashes or grep your way to finding the exact one you need. My command will typically look something like this, “hashcat –example-hashes | grep -B 1 ‘md5’.”
**
After searching for the correct hash mode and finding the path to our rockyou.txt wordlist, there’s only one more thing to do. Create a file, it doesn’t matter what the name or extension is, and paste the MD5 hash of “password123” inside. I’ll be naming my hash file as super_secret.hash. When we combine all of our flags and hacking goodness, we should end up with a command as such “hashcat -m 0 super_secret.hash rockyou.txt”
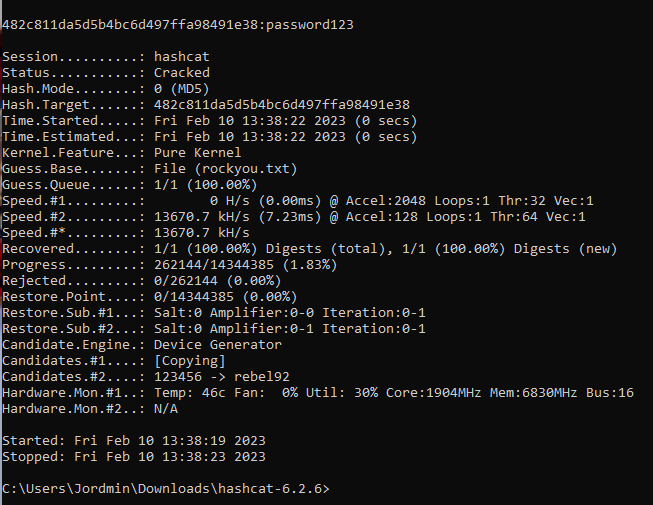
Sure, your first thought might be “why are you using Windows?” My response to that would be to tell you that my virtual machine broke before I wrote this post. However, your second thought is surely not a thought at all as the adrenaline of cracking my super secret password washes over you. As you can see Hashcat made quick work of our beloved password. Let’s try to crack a much more secure password, “pAsSwOrD135”. After updating my super_secret.hash file with the MD5 hash of “pAsSwOrD135” I fired up Hashcat for another go.
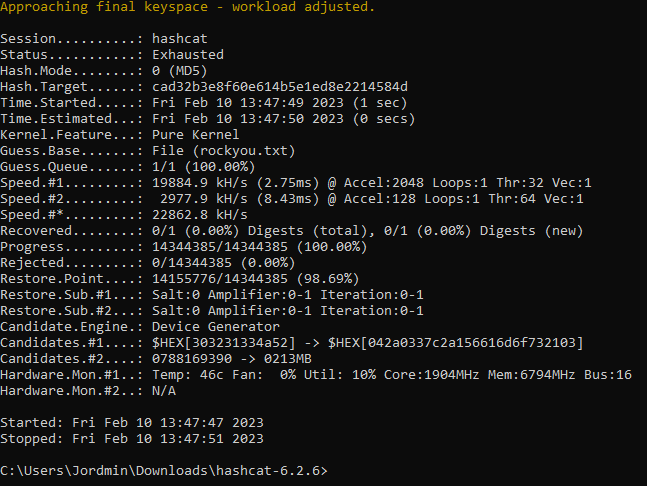
Well that surely isn’t as excited as our last run, but it does bring Hashcat’s one hinderance to the table. Just like a hash is only as strong as the plaintext password, Hashcat is only as strong as the wordlist you provide it. While discussing every wordlist on the Internet is surely out of the scope of this blog post, this is something you should keep in mind. My one recommendation would be to check out SecLists on Github, but not even that is a one-stop password cracking list by any means.
Cracking hashes, while trivial in the example above, is not always an easy feat. Some algorithms will require much more computational power per hash or you may even run into a database of salted passwords. For CTF/ challenge purposes usually passwords are limited to smaller lists that will generally take under twenty minutes to crack, however in the real world that isn’t quite the case. Identifying which hashes can and cannot be cracked may be a time consuming venture, at times it may turn up nothing at all. As with all things, be patient and continue to make educated attempts for the best chance of success.