
What makes a bad password? You might say anything under eight characters, only alphanumeric, or passwords based on a person’s interests is a bad password. While you would be correct to state the previously mentioned qualifiers, over the years, I have discovered another bad practice that tanks an organization’s password security: templated passwords.
Let me catch you up to speed if you’ve never belonged to an organization that uses templated passwords. Templated passwords are an ineffective solution to a properly implemented password complexity requirement. Below are two examples of templated passwords I have encountered in the wild.
1: Upper, lower, number, number, number, number, number, symbol
2: Six-character word with two digits intersected at the second character
Both of these templates meet the traditional “eight characters or above” requirement and are semi-randomly generated. On paper, passwords generated by this template aren’t the worst thing in the world. Much like security-by-obscurity, the danger is realized when knowledgeable attackers reveal these patterns.
When security professionals talk about a password’s “strength,” they’re really referring to the password’s key space. Key space is the set of all possible keys in a given format. Key space is calculated using a relatively simple mathematical formula- k^n (where k is the key space for a single character and n is the total number of characters). Using this formula, let’s calculate a few different key spaces.
8-character password with only lowercase = 26 ^ 8 = 208,827,064,576
8-character password with mixed cases = 52 ^ 8 = 5.3459729e+13
8-character password with mixed cases, numbers, and common symbols = 76 ^ 8 = 1.1130348e+15
As you can see, the larger the individual key space, the drastically larger the overall key space becomes. You may now be catching on to why templated passwords present attackers with a unique opportunity to crack an organization’s passwords. Let’s calculate the key spaces of the two templates presented above. To do that, we’ll need to switch up our formula slightly.
1: (26^1) * (26^1) * (10^1) * (10^1) * (10^1) * (10^1) * (10^1) * (14^1) = 946,400,000
2: (26^1) * (26^1) * (10^1) * (10^1) * (26^1) * (26^1) * (26^1) * (26^1) = 30,891,577,600
Numbers don’t lie. Despite our templates following “best practices-” all of the passwords in their key spaces are weaker than a traditional eight-character lowercase password! Most articles online leave off here, case-closed, point-proven. Instead, I think it’s only appropriate to implement some real-world hacking. Let’s put these numbers to the test and attempt to crack ten NTLM (Windows operating system) passwords to see how ineffective these templated passwords truly are.
Crunch is a wonderful tool built into the Kali Linux operating system. Crunch is one of those tools that does a simple job really well. In theory, Crunch is nothing more than a wordlist generator. Crunch’s power comes from its speed and ease of use. Referencing the manual page, we can use simple one-liners to generate entire wordlist dictionaries.
1: Crunch 8 8 -t ,@%%%%%^ -o template-1.dict
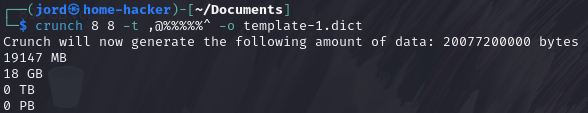
2: Crunch 8 8 -t @@%%@@@@ -o template-2.dict
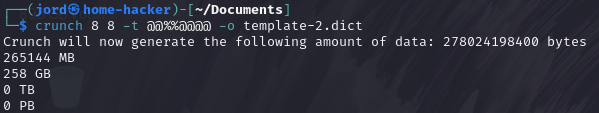
Side Note: Unfortunately, my Kali Linux machine only has 100 GB of storage. The second dictionary list requires around 258 GB, so you’ll have to take my word for it!
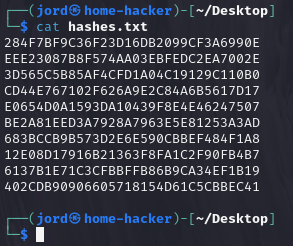
I’ll use CyberChef to generate the ten NTLM password hashes for cracking. Never heard of CyberChef? Do yourself a favor. (link) Here’s a look at the passwords I’ll use for the first test.
With our dictionary file ready to go, all that is left to do is fire up Hashcat. We’ll run a dictionary attack (mode 0) against NTLM hashes (code 1000). In addition, I’ll run the optimized kernels with option –O.
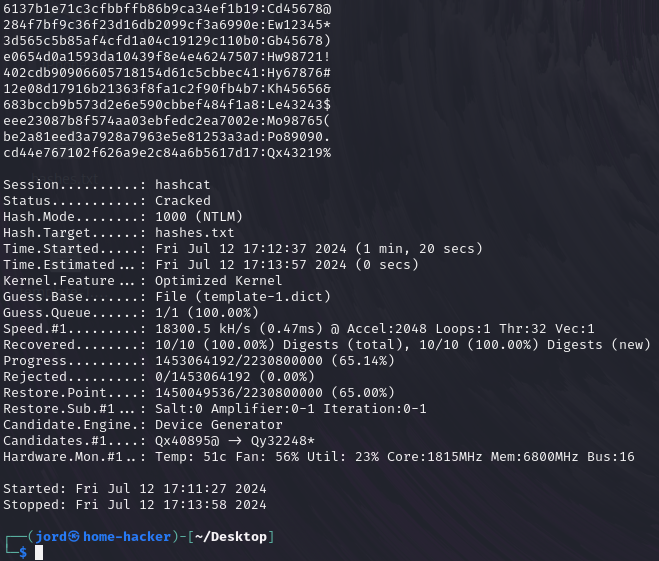
Utilizing the Crunch wordlist with Hashcat enabled us to crack ten NTLM-hashed passwords in only two minutes! While I’m not going to put my poor 3070 through the stress of brute-forcing the ten hashes, I was certainly curious. Firing up the correct command to brute-force our hashes, Hashcat estimated it would take around two and a half days. If this isn’t a case to ban templated passwords, I need to know what is!