
Computers are complex machines and, unfortunately for us IT people, that will only get worse with time. Our human minds can’t begin to comprehend all the execution cycles happening as we load up our favorite website, whitehatways.com. Our systems are constantly running hundreds of background tasks. Thankfully, just as much as systems complete background tasks, they also log them.
Logs, while there is no mandatory standard, are typically comprised of timestamps and a small message explaining what happened and when. System administrators often look to logs for answers when adverse events occur. A system crashed? Check the logs. An application mysteriously stopped working? Check the logs. Servers were compromised in a security breach? Check the logs! What happens if there are no logs?
Reliable logs cannot be taken for granted and are not a guarantee in the event of compromise. Skilled attackers will likely attempt to clear their tracks, and unfortunately for us, that typically means erasing our precious log files. Reverse engineering an attacker’s actions without solid logs will be nearly impossible. Well, it’s a good thing that modern operating systems implement military-grade, impenetrable, state-of-the-art protections on these log files! Right?
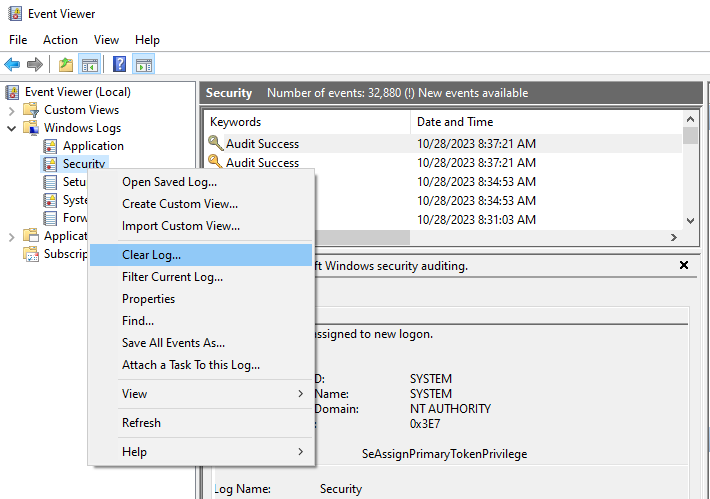
Unfortunately, log files are just standard text files- albeit slightly cryptic on Windows machines with their EVTX format. Operating systems don’t offer much protection for log files out-of-the-box besides rudimentary permission locks. Attackers who obtain certain permission levels may clear and manipulate logs to their heart’s content.
The answer to our theoretical crisis is to use a Security Event and Information Management (SIEM) solution. SIEM platforms allow system administrators to orchestrate a central logging server where systems deliver their logs auto-magically. In our example before, regarding a compromised network node, the SIEM server would still host the logs the attacker attempted to remove. An attacker who has achieved administrative privileges over a system could, in theory, prevent continuous logging by stopping the SIEM service, but the previous logs would still be recorded. There is no way for an attacker to remove the logs recorded by the SIEM other than hacking into the SIEM server itself.
Ensuring log integrity, of course, is not the only benefit of implementing a SIEM solution in an environment. SIEM solutions aid administrators in centrally reviewing logs, meeting compliance goals, and many other daily tasks. However, as security personnel, understanding safeguards to logs from a red and blue-team lens is vital.